[ad_1]
The infamous Emotet botnet has been linked to a mannequin new wave of malspam campaigns that revenue from password-protected archive data to drop CoinMiner and Quasar RAT on compromised functions.
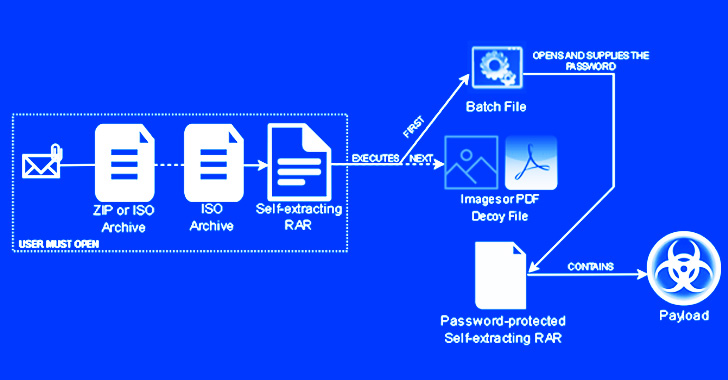
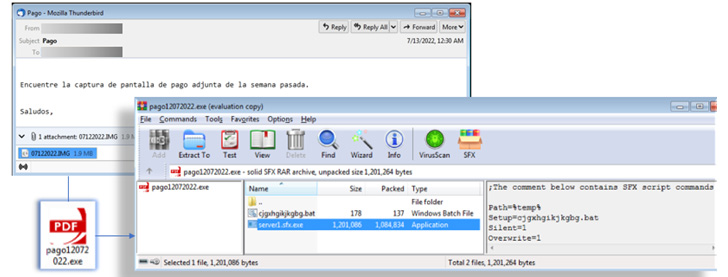
In an assault chain detected by Trustwave SpiderLabs researchers, an invoice-themed ZIP file lure was discovered to include a nested self-extracting (SFX) archive, the primary archive displaying as a conduit to launch the second.
Whereas phishing assaults like these historically require persuading the purpose into opening the attachment, the cybersecurity company talked concerning the promoting advertising and marketing marketing campaign sidesteps this hurdle by making use of a batch file to routinely current the password to unlock the payload.
The primary SFX archive file additional makes use of every a PDF or Excel icon to make it seem legit, when, genuinely, it accommodates three elements: the password-protected second SFX RAR file, the aforementioned batch script which launches the archive, and a decoy PDF or picture.
“The execution of the batch file ends within the organize of the malware lurking all by the password-protected RARsfx [self-extracting RAR archive],” researchers Bernard Bautista and Diana Lopera talked about in a Thursday write-up.
The batch script achieves this by specifying the archive’s password and the vacation spot folder to which the payload will likely be extracted, along with launching a command to point the lure doc in an try and cowl the malicious practice.
Lastly, the an an an infection culminates all through the execution of CoinMiner, a cryptocurrency miner which will additionally double up as a credential stealer, or Quasar RAT, an open present .NET-based distant entry trojan, relying on the payload packed all through the archive.
The one-click assault methodology might also be notable in that it effectively jumps earlier the password hurdle, enabling malicious actors to hold out a variety of actions paying homage to cryptojacking, data exfiltration, and ransomware.
Trustwave talked about it has acknowledged a rise in threats packaged in password-protected ZIP data, with about 96% of those being distributed by the Emotet botnet.
“The self-extracting archive has been spherical for a extremely very very long time and eases file distribution amongst finish prospects,” the researchers talked about. “Nonetheless, it poses a safety danger provided that file contents will not be merely verifiable, and it will presumably run instructions and executables silently.”
[ad_2]